
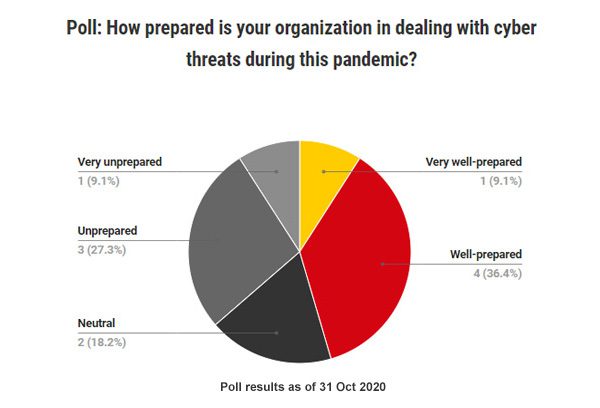
6 ways to protect supply chains against Covid-19 cyber threats

Amid the chaos caused by the pandemic on healthcare systems and economies, some malicious cybercriminals have taken full advantage of the distractions and existing vulnerabilities to launch cyberattacks against companies.
In many instances, they succeed. One of the high-profile companies to be hit was Japanese automaker Honda, which, like many other corporate giants, was already reeling from the coronavirus fallout.
In June this year, the company’s manufacturing plants around the world were forced to suspend production for days after they discovered a breach that compromised access to its internal IT systems.
At this time Honda Customer Service and Honda Financial Services are experiencing technical difficulties and are unavailable. We are working to resolve the issue as quickly as possible. We apologize for the inconvenience and thank you for your patience and understanding.
— Honda Automobile Customer Service (@HondaCustSvc) June 8, 2020
According to cybersecurity experts, the file-encrypting ransomware program — later identified as Snake/Ekans — specifically targets industrial control systems with a high level of intentionality. For Honda, the ransomware encrypted files and demanded a ransom from the company to restore the files.
The sophistication and creativity of such cyberattacks continue to frustrate companies across all industries during this pandemic, with the healthcare sector being one of the worst-hit.
“Ransom payment to ransomware operators is no guarantee of successfully securing one’s systems and data. Law enforcement officials generally discourage the practice to apprehend those responsible,” said Shehrina Kamal, Product Director, Risk Monitoring for DHL Resilience360, a supply chain risk management software.
Instead of releasing data securely upon payment, newer ransomware operators tend to intentionally publish and expose, or “doxx” their targets for malicious ends, explained Kamal.
To minimize potential exposure to Covid-19 cyber threats, supply chain professionals are encouraged to initiate these mitigating measures recommended by DHL Resilience360 in its latest report:
1. Maintain data backups
Supply chain managers can work with suppliers to verify or stipulate that they are maintaining system backups. Regular and thorough backups are the best mitigation against ransomware, regardless of the company’s inclination to accede to ransom demands.
In the event of a cyberattack, having a proper backup will also help to reduce downtime which could hinder operations if unresolved quickly. This indicates a growing necessity to adopt best practices in this aspect.
Companies that maintain ongoing, comprehensive backup programs should create an effective “mirror” of current operations, enabling them to quickly jump to a parallel system in the event of an attack.
2. Know your defenses
Organizations must be mindful when assessing cybersecurity loopholes in their supply chain. Firewall and vulnerability mitigation should be prioritized for suppliers with the highest level of access to the company’s network, and those with the greatest exposure to threats.
This measure of exposure considers factors such as industrial control systems known to be vulnerable, or within a location or an industry-recognized target for frequent attacks. According to technology giant IBM’s latest X-Force Threat Intelligence Index, which assesses the threat landscape and cybersecurity risk trends, the transportation sector ranks among the most vulnerable to cyberattacks.
To protect their supply chain and logistics operations from disruptions, companies have to keep abreast of the cyber threat environment to further enhance the organization’s defense posture.
3. Enhance physical security
Besides improving cybersecurity measures, companies should not neglect physical security arrangements. It is equally vital for companies to verify that its suppliers implement adequate measures to prevent their physical office environments from being compromised.
While offices remain below normal occupancy due to the pandemic, companies should ensure that supplier facilities have secured any physical documents with personally identifiable information (PII), financial information, or credentials to reduce the chances of any exposure during an attack.
4. Synchronize threat preparation and response
There have been instances of multinational companies being hit as part of targeted attacks more than once in a span of a few years.
The likelihood of repeated attacks means that companies have to take necessary precautions to ensure that their suppliers have business continuity plans in place to react appropriately should a cyberattack occur.
Adequate preparation to enhance coordination and minimize confusion, if a crisis strikes, can allow all parties involved to save time and act in unison to maintain supply chain agility.
5. Understand the systems of your suppliers
Having an overview of the technological tools, hardware, equipment, and operational systems of suppliers can empower those responsible for information security in the company to anticipate potential disruptions and plug any loopholes.
“The knowledge of the different systems will also help supply chain managers to play a more proactive role in safeguarding the companies’ suppliers against cyber threats,” said Daniel Boccio, Analyst, Risk Intelligence and cyber threat expert at DHL Resilience360.
6. Ensure social engineering awareness
To stay vigilant and prepared, companies should collaborate with IT partners to conduct realistic, frequent, and varied phishing testing at the supplier level and across the supplier network to identify vulnerabilities. This reduces, to the greatest extent possible, the threat field that a potential hacker can exploit.
It is also recommended that companies build information-sharing relationships with law-enforcement bodies to further enhance awareness and protection, while encouraging suppliers to do the same.
Supply chain managers must also collaborate with IT teams to determine the impact of a disrupted business, obligations to maintain cybersecurity, and adhere to information technology standards such as the ISO/IEC 20071/2.
This article was adapted from a DHL Resilience360 report.
ALSO WORTH READING












 English
English